Cybercrimes are getting increasingly popular as they are more lucrative compared to other types of criminal acts. And what makes it so enticing is that the barrier to entry is not very high. Even a newbie hacker can get ransomware on subscription. There is a low chance of getting caught, so the risk of severe implications does not deter the criminals.
As digital dependence is increasing for all business operations, including business productivity tools, any vulnerability in the systems being used can create havoc in our lives.
The areas being attacked and the impacts of these unfortunate events are growing at a startling pace. This leads us to a critical question that bothers everyone associated with the business, no matter what level they enjoy in the organization. How can you protect your business from cyber-attacks?
You don’t just have to be worried about the skill level of the hacker, but also the broad range of threats from viruses, ransomware, malware, social engineering, illegal hacking, and more that continue to raise fear levels for lots of organizations.
Irrespective of where your security programs stand, there are ways to strengthen your defences to block these attacks and lessen the potential damages.
Assess your cybersecurity:
Can you build sufficient defences without knowing where you stand? Regular assessment of your cybersecurity is key to preparing a sound security program as it informs you of your strengths and weaknesses.
Starting with a clear evaluation helps you chalk out the right steps for securing your environment. It enables you to prioritize your resources and prevent waste of time and money. Once you have done a gap analysis, you can even take your assessment to the next level by applying risk management techniques. Get your priorities right and analyze the items that can be deferred.
Train your staff:

The chain is only as strong as the weakest link. Most cyber-attacks result from the vulnerabilities opened by uninformed or careless employees.
Train your staff on using strong passwords and not falling for social engineering or phishing attacks. Ensure they know of the tricks used by cybercriminals – they must be aware of how to identify suspicious phone calls and emails, especially the ones that seem legitimate on the face. Inform them of steps they should take if they spot something fishy.
Adopt strong security policies in line with the best practices and ensure your employees are well-versed in the processes. Encourage a team environment where everyone watches out for one another and acts as an extended security team.
Keep your software updated:
Do not run outdated versions of any software. Older releases are prone to zero-day attacks and exploits, which can result in network penetration, stolen information and heavy damages.
While some software such as anti-virus programs may have the auto-update feature, others may not have this feature. Check for new releases of your software periodically.
Implement vulnerability detection processes to check for exposed loopholes and missing patches so that you can install the required updates.
Use an SSL Certificate to protect your data:
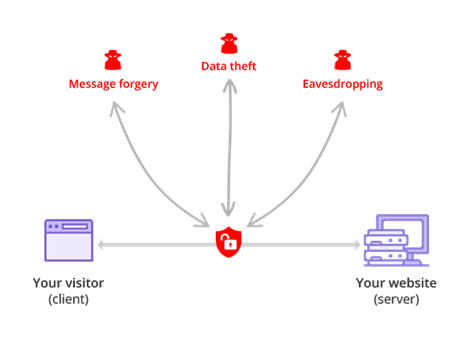
Install an SSL certificate to switch to the more secure form of the traditional HTTP protocol, the HTTPS (hypertext transport protocol secure). It will encrypt the communication channel so all the data being transmitted between the user’s browser and your web server is protected from the peering eyes of anyone who may be listening on the wire. If you have multiple domains to be protected, consider getting a multi-domain wildcard SSL certificate to save money and effort.
Not only does SSL keep your user’s information secure, but it also boosts their confidence that leads to increased sales and conversions for your business. Also, you get an SEO boost by the search engines for adopting SSL.
Monitor round-the-clock:
Implement round-the-clock monitoring so you are always vigilant and can catch the attacks before severe damage.
Use SEIM (Security Event and Incident Monitoring) to get alerted for data irregularities and suspicious activity that may be indicative of an attack. Strengthen your security operations centre so they can act promptly when you are under fire – their services can help you with analyzing the alerts and narrowing down the ones that may harm you.
Create an incident response plan:

Never assume that any defences you implement will be 100% effective. Create a well-thought-out incident response plan so your company can react swiftly and effectively if you do get hit.
A good response plan will layout the escalation path to be used, so the appropriate teams get notified timely when a problem is observed. It must clarify the steps to be taken, assign responsibilities for the response, and also dictate communication mechanisms to inform leadership, outside stakeholders, and the general public, when needed.
Provide least access privileges:
Make sure you narrow down the privileges to only what is needed by a role, level, job function, and team member. In short, only the administrators should have full access to networks, systems, and tools.
The remaining employees should not have any more access than what is needed for them to perform their job. So, if a hacker does get hold of someone’s credentials, the damage will be limited to the rights the person has.
Ensure physical security:
Don’t ignore the security of your physical space while you secure your digital assets. In many instances, attackers get login credentials, infrastructure details, trade secrets, and other exploitable/valuable information by being physically present in your data centres and offices.
Adopt security best practices such as video surveillance, badged entry, and supervising visitors. Train your staff to protect their surroundings when they are away by staying vigilant while working remotely during travel or when accessing public spaces. Your personnel should keep their screens, conversations, and calls private in external environments.
Use cyber intelligence:

While you cannot overlook cybersecurity assessments to keep an eye on your blind spots and have to implement mechanisms to monitor your networks and systems, constantly to detect suspicious activities and intrusions, it is equally critical to keep monitoring the external landscape.
Use cyber intelligence tactics such as dark web monitoring to gain deeper insights into attacks that may be in planning stages, the criminals who are likely to attack you, and how they may do it. You may also be able to detect information such as credentials that may already be doing rounds in the underground market. This knowledge will help you craft a precise defence strategy.
Access 3rd party vendor risk:
A lot of breaches that have happened at large companies were caused by the vulnerabilities found by hackers in small 3rd party suppliers. Ask questions such as: How do they protect their data, systems, and networks? How do they dispose of data? What regulations do they adhere to? Do they avert their employees?
Implement a strict process to evaluate the security measures adopted by your key vendors. Make periodic updates to your assessments and integrate them into incident coordination and threat monitoring, so they take care of their part and not place you at risk.
Stay aware of hardware thefts:
If your business has adopted a BYOD (bring your device) policy, allowing employees to use their mobile devices for work, have data protection mechanisms in place. Try to track these devices too, if possible. You must be able to block the login if a device gets stolen.
Ensure that all the information stored on these devices is encrypted. While most cybercrimes deal with online digital information, lost devices can also be equally harmful. There is a possibility of an attacker gaining access to the information on the stolen device and using it for malicious purposes, including cyber-attacks, so prepare accordingly.
Conclusion:
Online attacks and data breaches can cause a lot of harm to your business, including financial loss, legal liability, and even a complete shutdown in extreme cases. It takes due diligence and effective cybersecurity strategies to protect your business from cyber-attacks. Combine the tips we have listed above with common sense to circumvent hacking attempts. The best part is that these solutions save you money as they align your cybersecurity activities with the threats.